Cloudflare Research: Post-Quantum Key Agreement
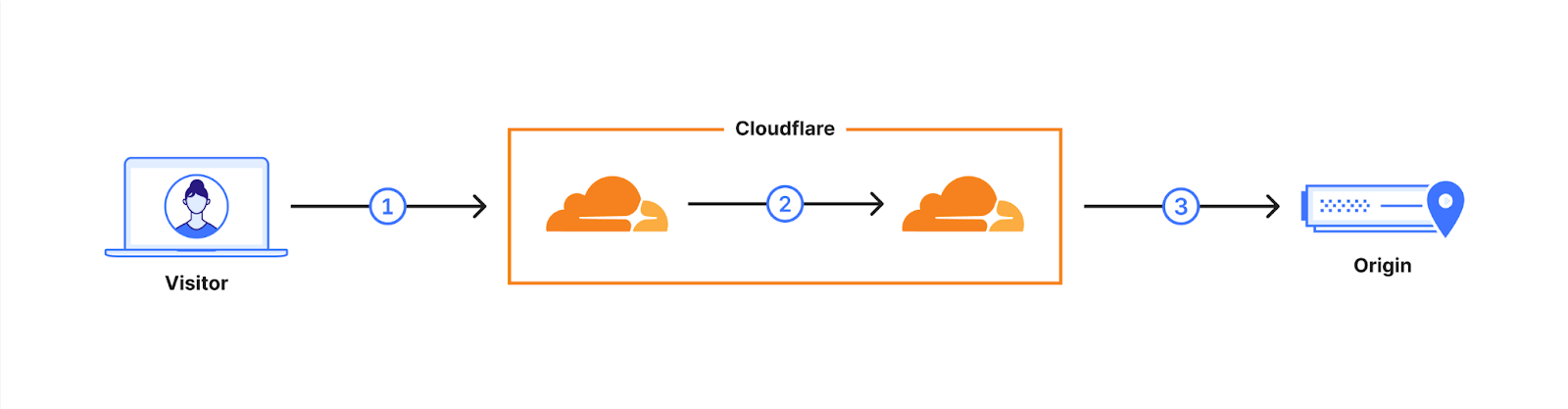
On essentially all domains served (1) through Cloudflare, including this one, we have enabled hybrid post-quantum key agreement. We are also rolling out support for post-quantum key agreement for connection from Cloudflare to origins (3). Check out our blog post the state of the post-quantum Internet for more context.
Checking connection …
Deployed key agreements
Available with TLSv1.3 including HTTP/3 (QUIC)
| Key agreement | TLS identifier | |
|---|---|---|
| X25519MLKEM768 | 0x11ec (recommended) | |
| X25519Kyber768Draft00 | 0x6399 (obsolete), 0xfe31 |
|
0xfe30 |
Software support
See the developer docs for a listing of software support for post-quantum key agreement.
References
- State of the post-quantum Internet in 2025
- tldr.fail explains how large post-quantum ClientHello could break buggy software.
Contact
You can reach us directly at ask-research@cloudflare.com with questions and feedback.